Solutions
Agile Cyber Tech Solutions
- Penetration Testing
- Managed Detection & Response (MDR) Solution (SOC as a service)
- M365 Endpoint Detection & Response (EDR)
- M365 Co-Pilot AI Cyber Security Preparation
- Secure Email Gateway, Continuity & Archive Solutions
- Essential Eight Maturity Model Implementation
- Vulnerability Scanning (Health-check/ IR Service)
- Remediation of Compromised Network Elements
- Improve Enterprise Organisation’s Security Posture
- Security Tools Implementation (M365 Defender, DNS, DMARC, Firewalls)
- Security Maintenance Updates for M365 Security, Networking & Firewalls
- Incident Response Service Solution Including Ransom Negotiation
Agile Managed Services Microsoft Security Packages
- SECURE your business digital workspace,
- BUILD a solid & stable foundation and
- EMPOWER your employees to achieve more by creating a work environment that's intelligent, flexible, and Agile.
Microsoft 365 Security
Licensing, Maintenance Technical Services
Discover a more efficient and secure digital future with our tailored services. We expertly manage Microsoft 365 licenses and Azure Infra, streamline Microsoft Teams deployment, and provide Power BI expertise for data visualization.
Your M365 & Azure Subscription with AgileTech includes VIP Support. We’ll assist you with your support Microsoft incidents and connect you with Microsoft Support for faster resolution.
Robust security, confidently navigate Azure migrations and billing optimization are some of the benefits of AgileTech Subscription Management, coupled with VIP Support. We’re your trusted partner in unleashing your secure digital potential.

Agile Cyber Tech

Awareness Training Solutions

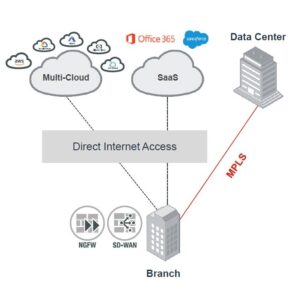
SD-WAN Security & Network Consolidation
Network consolidation involves simplifying and streamlining an organization’s network infrastructure. It typically includes reducing the number of physical network appliances and consolidating network services into a more centralized and efficient architecture.
Mimecast Email Security,
Archiving, Continuity & DMARC
Mimecast delivers enterprise cloud based email management services including Archive, Continuity and Security & Cyber Security Training
S1 boasts 100% SLA financially backed virus protection and 99% SLA on anti spam protection, making it the most comprehensive cloud based email security and compliance solution in the market. By switching your MX Records to point to the Mimecast platform, Multiple layers of malware and spam protection acts as your email bridgehead in the cloud stopping threats before they reach your network. Staff Cyber Security Training – Ataata provides unique modern training techniques, with predictive analytics to reduce employee security mistakes and solves companies security vulnerabilities due to employee human error. Mimecast + Ataata Intro Video

SD WAN, Security & Networking Convergence
- connectivity to all users and devices to applications with reduced latency
- monitor and secure enterprise traffic from a single, cloud-native platform
- protect and defend any roaming user
- provide visibility and control over all SaaS applications, sanctioned or otherwise
- capture deep insights from the endpoint all the way to cloud services