Home

“Agile” able to move and adapt quickly in a fast-paced dynamic environment…
- Agility is one of our most important differentiators.
- Agility enables us to deliver our Solutions & Services in an effective and timely manner.
- Results in faster customer service responsiveness and hassle-free procurement.
Incorporated in 2005, our mission is to help our Enterprise customer’s pain-points in IT Networks, Cyber Security & Procurement – to transform IT into a investment that returns true value to their respective organisations.
Agile designs, implements, secures and manages for the Enterprise
- Enterprise Networking
- Azure Infrastructure & Solutions
- Microsoft 365 Security Implementation
- M365 Copilot AI Preparation
- Cyber Security Products & Managed Services
- Power BI & Business Process Optimisation Services
- Data Centre Technical Services
- Advanced Penetration Testing Services
- Licensing & Support Subscription Management
- Endpoint & Adhoc Daily Procurement
- On-Prem/Hybrid Infrastructure (Servers/Storage)
- Network Managed Services
- Technical Services & Project Management
Agile Cyber Tech Solutions & Services
- Penetration Testing
- Managed Detection & Response (MDR) Solution (SOC as a service)
- M365 Endpoint Detection & Response (EDR)
- M365 Co-Pilot AI Cyber Security Preparation
- Secure Email Gateway, Continuity & Archive Solutions
- Essential Eight Maturity Model Implementation
- Vulnerability Scanning (Health-check/ IR Service)
- Remediation of Compromised Network Elements
- Improve Enterprise Organisation’s Security Posture
- Security Tools Implementation (M365 Defender, DNS, DMARC, Firewalls)
- Security Maintenance Updates for M365 Security, Networking & Firewalls
- Incident Response Service Solution Including Ransom Negotiation
Agile Managed Services Microsoft Security Packages
- SECURE your business digital workspace,
- BUILD a solid & stable foundation and
- EMPOWER your employees to achieve more by creating a work environment that's intelligent, flexible, and Agile.

Microsoft 365 Security
Licensing, Maintenance Technical Services
Discover a more efficient and secure digital future with our tailored services. We expertly manage Microsoft 365 licenses and Azure Infra, streamline Microsoft Teams deployment, and provide Power BI expertise for data visualization.
Your M365 & Azure Subscription with AgileTech includes VIP Support. We’ll assist you with your support Microsoft incidents and connect you with Microsoft Support for faster resolution.
Robust security, confidently navigate Azure migrations and billing optimization are some of the benefits of AgileTech Subscription Management, coupled with VIP Support. We’re your trusted partner in unleashing your secure digital potential.
Agile Cyber Tech
Awareness Training Solutions
Boost your organization’s cyber defense with our comprehensive Cyber Security Awareness Training. Equip your team with the skills to identify and combat a range of cyber threats, from phishing to data breaches. Our expertly designed modules and hands-on simulations cultivate a culture of cyber resilience. Prepare your workforce to safeguard sensitive data and maintain digital integrity. Stay ahead of cyber threats with our proactive training solutions.

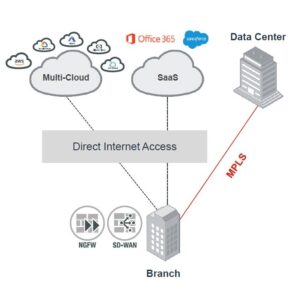
SD-WAN Security
& Network Consolidation

SD-WAN technology optimizes the performance and management of wide-area networks by using software-based control and automation. In the context of security, SD-WAN solutions often include features like encryption, firewall capabilities, and threat detection to enhance the security of network traffic over wide-area connections.
Network consolidation involves simplifying and streamlining an organization’s network infrastructure. It typically includes reducing the number of physical network appliances and consolidating network services into a more centralized and efficient architecture.
Cyber Security
Managed Detection & Response

Elevate your cyber defense & mitigate Cyber risks with our Cyber Security Managed Detection & Response services provided by our Cyber SOC as-a-service Partner, Arctic Wolf. As a global leader in MDR, their proactive approach leverages cutting-edge technology and expert analysts to monitor your digital environment 24/7.
$1b investment in the Platform, with up to $1m USD Financial Warranty for customers in the event of a breach, provides confidence and piece of mind for your organisation.
Arctic Wolf’s MDR swiftly detect and respond to threats & suspicious behaviour, ensuring that your organization remains one step ahead of cyber adversaries. Protect your critical assets and maintain peace of mind with our robust, managed security solutions.
See short clip: How the Arctic Wolf® Platform Stops Active Ransomware – YouTube
Mimecast Email Security, Archiving, Continuity & DMARC
S1 boasts 100% SLA financially backed virus protection and 99% SLA on anti spam protection, making it the most comprehensive cloud based email security and compliance solution in the market. By switching your MX Records to point to the Mimecast platform, Multiple layers of malware and spam protection acts as your email bridgehead in the cloud stopping threats before they reach your network. Staff Cyber Security Training – Ataata provides unique modern training techniques, with predictive analytics to reduce employee security mistakes and solves companies security vulnerabilities due to employee human error. Mimecast + Ataata Intro Video

Solutions
SD WAN, Security & Networking Convergence
- connectivity to all users and devices to applications with reduced latency
- monitor and secure enterprise traffic from a single, cloud-native platform
- protect and defend any roaming user
- provide visibility and control over all SaaS applications, sanctioned or otherwise
- capture deep insights from the endpoint all the way to cloud services
Our Services
Microsoft 365 Security - Licensing, Maintenance Technical Services
- Microsoft 365, SPLA, Open Value Subscription License Management
- Microsoft 365 Intune Design, Migration & Implementation
- Microsoft Teams Design & Implementation, flip the collaboration switch in your organisation
- Power BI: Build Dashboards & Design a Data model Technical Services
- Windows Defender ATP Design & Deployment
- Azure Cloud Migrations Technical Services
- Azure Billing Management & Optimisation
- CASB- Control Cloud Apps, DLP, Data Security, Threat Protection, Compliance & Web Proxy
Advanced Penetration Testing
- Identify vulnerabilities: The main goal of a penetration test is to identify vulnerabilities that could potentially be exploited by malicious actors. This includes weaknesses in software, misconfigurations, poor security practices, or design flaws.
- Assess security controls: A penetration test evaluates the effectiveness of security controls implemented within an organization’s infrastructure, systems, and applications. It helps in determining whether the existing security measures adequately protect against attacks.
- Measure risk levels: By exploiting vulnerabilities, a penetration test helps in quantifying the level of risk associated with the identified weaknesses. This information is useful for prioritizing remediation efforts and allocating resources to address critical vulnerabilities.
- Test incident response: Penetration tests often simulate real attacks to test an organization’s incident response capabilities. By evaluating how well the organization detects, responds to, and mitigates the simulated attacks, it can identify areas for improvement in their incident response procedures.
- Validate compliance requirements: Penetration tests can help organizations demonstrate compliance with industry regulations or security standards by assessing if the required security controls are effectively implemented and providing evidence of their effectiveness.
- Provide recommendations: A comprehensive penetration test report includes recommendations for improving security posture. It suggests remediation measures, best practices, and security enhancements to mitigate identified vulnerabilities and strengthen overall defenses.
Managed Services & Technical Support
efficient operation of your IT environment:
- Technical Services & Project Management
- Network Support Agreements
- 24/7 Emergency Response & Support (Managed Services)
- License & Subscription Management
- Ongoing Security & Network Health Checks
Microsoft 365 Enterprise & Microsoft Teams
- Tailor your Teams workspace to include key cloud services
- Explore data and get updates from the apps your teams use every day
- Create custom channels based on work streams or topics
- Pin commonly used files and websites for easy reference
- Add bots that work on your team’s behalf